Focusing on the wrong chapter Let’s start with a groundbreaking(?) discovery. Concepts like “Entities”, “Value Objects”, “Repositories”, “Services”, referred as tactical patterns in DDD, are not discovered or originally proposed by DDD. They exist in the world of OOP before DDD[1]. The significant contribution of DDD is that it is enabling us to first think…
Design Patterns in Action: Decorator and Symfony Lock component.
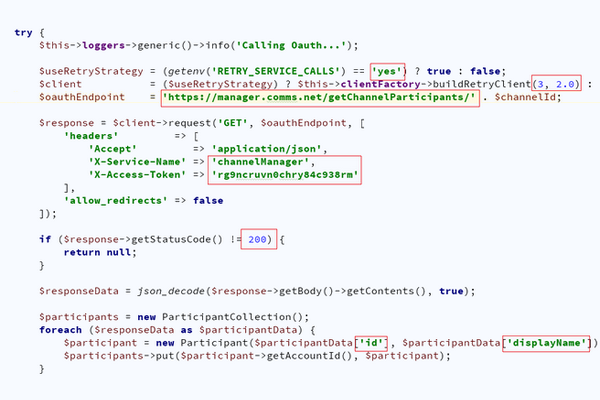
Today, we have a look inside the symfony/lock component. As stated in https://symfony.com/doc/current/components/lock.html , “The Lock Component creates and manages locks, a mechanism to provide exclusive access to a shared resource.” The given example describes the idea: $factory = new LockFactory($store); $lock = $factory->createLock(‘pdf-invoice-generation’); if ($lock->acquire()) { // The resource “pdf-invoice-generation” is locked. // You…
PHP, you are interpreted. Join the club!
There is some confusion out there about which high-level programming languages are interpreted and which are compiled. And every time someone mentions that PHP is an interpreted one, many PHP developers seem like feeling a bit ashamed about it. Mostly because they think that PHP is the only, or one of the few, programming languages…
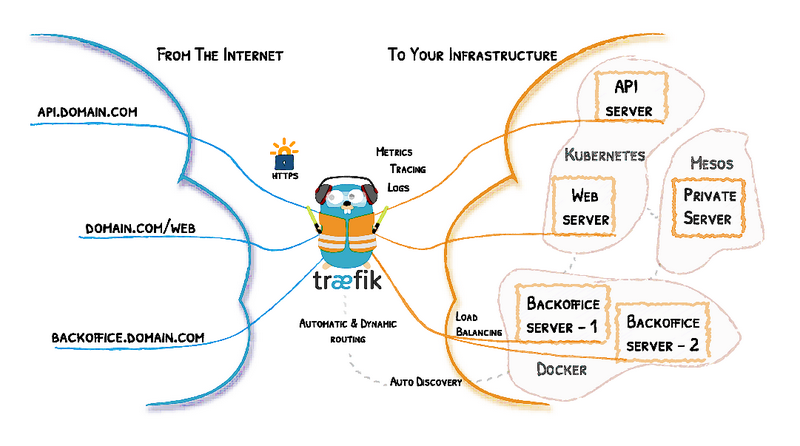
Setting up a development environment using Traefik v2
In this post, we explore a basic development environment setup using Traefik. Basic concepts Traefik is an open-source Edge Router. “Edge” means that is supposed to live and handle traffic on the edge of your network. It is not supposed to be used in routing internal traffic within your infrastructure but only traffic between external…
PHP asynchronous programming with Swoole: Part 2
This is the second post about Swoole and it contains code samples that take advantage of Swoole asynchronous functions and coroutines. The first post can be found here. HTTP Requests Asynchronous 1: We put each request in a separate coroutine and pass them a channel through which they will pass to us the results of…
PHP asynchronous programming with Swoole: Part 1
This first part will provide some basics on working with Swoole and it is meant to work as an introduction to the code samples we will include in the second part. Slowly but steadily, mostly in the last 5-6 years, PHP is making steps to the direction of asynchronous programming. Although ReactPHP was showing the…
Queueing with SKIP LOCKED
In 2018, at last, MySQL (version 8) decided to add support to the famous “SKIP LOCKED” feature. Other RDBMS like Oracle and SQL Server support this feature for more than 15 years and PostgreSQL added support in 2016. If this is the first time you hear about this, it is a flag that tells the…
Passing…Traits
Let’s start with a definition: “a trait is a concept used in object-oriented programming, which represents a set of methods that can be used to extend the functionality of a class” (Wikipedia) So, a set of methods. No properties. No extra state representation. After all, as you may know, this is the fundamental difference between…
Removing code literals
Every piece of software contains literals (usually numbers, strings or booleans). These are values related to application configuration, parts of the business logic, natural or language constants, etc.. We have learned to replace many of these values with variables, constants or function calls for various reasons (security, manageability, readability, expressivity,…), which we are not going…
Truncating decimals from summands and sum
This is a problem that you may have run into at some point. Especially, if you had to display or print the components of a price using less decimals than the decimals used for the calculations. Cutting-off decimals after the calculation has taken place can lead to inconsistency between the summands and the sum. In…
Design patterns in Action: Flyweight and Enumerated types
Flyweight pattern is not a pattern that you will come across very often in web applications. Most web applications are just serving incoming HTTP requests, a task that lasts just a few milliseconds. So, memory usage is not really a consideration for their developers. However, there is one area where you can see this pattern…
A long cheatsheet for Redis
Setting up Redis: (on Ubuntu 16.04) Install Redis server apt-get install redis-server Enable Redis as service (start on system boot) systemctl enable redis-server.service Note: The service configuration can be found at: /etc/systemd/system/redis.service There you can see that Redis will be running as user redis: User=redis Group=redis The Redis server will always restart after reboot: Restart=always…